Operations | August 1, 2012 | 3 min read
No More Accidental Deletion of Admin User
Removed “Delete” option from listing of user accounts, for the admin account. This will prevent the admin account from being accidentally deleted. Example:
Removed “Delete” option from listing of user accounts, for the admin account. This will prevent the admin account from being accidentally deleted.
Example:
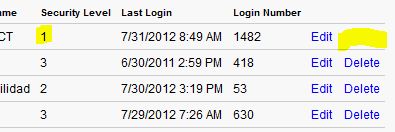
In today’s digital environments, an admin account isn’t just another user—it’s the gateway to critical configurations, billing options, and user rights. Accidentally deleting one can lead to operational setbacks, security lapses, or data loss. ReservationKey’s August 1, 2012 update addressed this head-on by removing the “Delete” option from admin accounts. But beyond hiding buttons, what strategies can your organization adopt to safeguard against this error?
Why Admin Account Deletion Is a Major Risk
- Ultimate Access Loss: Without an admin account, you lose control over system settings and user permissions.
- IR Recovery Options Are Limited: While some platforms offer backup and restore options, it’s not always easy or fully reliable.
- Security Vulnerabilities: Losing an admin account can force organizations to create a temporary account under urgency—opening doors to errors or breaches.
1. Hide or Remove “Delete” as ReservationKey Did
ReservationKey’s update sets a great example. By removing the “Delete” button where it counts, they drastically reduce the chance of unintended deletions . Tip: In your system, evaluate whether admin roles need deletion at all. Often, disabling or masking them is a safer option.
2. Implement Protection Flags in Directory Services
Windows Active Directory includes a "Protect object from accidental deletion" flag in the object's security properties community.opentext.com. This simple toggle prevents deletions even if someone tries via a script or GUI. Tip: Audit your directory and enable this flag for critical OU and admin accounts.
3. Enforce Role-Based Access Controls (RBAC)
Grant deletion rights only to trusted roles—never universally. Enforce least-privilege RBAC and ensure robust logging is active so all deletions are accountable.
4. Introduce a “Soft-Delete” or Grace Period
Rather than permanently removing accounts immediately, move them into a quarantined state that holds them for, say, 30 days. This gives admins ample time to notice mistakes and restore access. Microsoft 365, for example, provides such a window with soft-deleted user retention.
5. Use Deletion Auditing and Reporting Tools
Tools like AdminDroid offer transparent auditing with details such as "who deleted whom" and “when,” plus scheduled reports for oversight. 📊 Tip: Set up weekly or even daily reports so errors are caught quickly.
Feature Comparison Table
StrategyEffortEffectivenessHide “Delete” for adminsLowHighEnable “Protect from deletion”LowVery HighRBAC for deletion rightsMediumHighSoft-delete with grace periodMediumHighAuditing & reporting toolsHighHigh
Final Takeaway
Admin accounts are vital—and vulnerable. Through UI safeguards, directory flags, RBAC, grace periods, and audit tools, you can build a multipronged defense against accidental deletion. ReservationKey’s “no-delete” approach is an excellent starting point, but combining it with technical and administrative controls ensures your system stays resilient, even against human error.
Click Here
Request A DemoGet A Free Trial Instantally
Frequently Asked Questions (FAQ)
Q1: Can I accidentally delete my only admin? A1: Yes, unless safeguards are in place. Removing “Delete” buttons, adding protection flags, and implementing role-based access control can prevent this risk.
Q2: What happens in soft‑delete? A2: Deleted accounts are hidden but retained for a set period (e.g. 30 days), allowing recovery without permanent loss.
Q3: Does Active Directory offer accidental deletion protection? A3: Yes—it includes a checkbox under Security → Advanced → "Protect object from accidental deletion." Enable it for key objects.
Q4: Are there tools to audit deletions? A4: Yes—AdminDroid and similar tools provide complete tracking of deletion events, including executor and timestamp .
Q5: How did ReservationKey handle this problem? A5: They simply removed the “Delete” option for admin roles in their UI, reducing mistakes without additional complexity .
Q6: What should I do if an admin is accidentally removed? A6: First, check if a soft-delete exists. If not, recreate the account and assign permissions based on backups, logs, or audit trails.